On Friday, the Small Business Administration (SBA) posted the final application for the Paycheck Protection Program for small businesses. This is the result of the Coronavirus Aid, Relief, and Economic Security (CARES) Act, a bill that was fast-tracked through Congress and signed by the President, part of which was to provide supplemental funding to businesses… Continue reading SBA’s Paycheck Protection Loan Program and the CARES Act
Category: Blog
Recovery Fatigue and the Disaster Lady 2.0
Hey folks! This has been quite a week. New COVID scams from hackers saying they have the cure to Dr. Fauci. Researchers announcing they are puzzled and don’t know why some folks get sick, while others just have mild symptoms. All of this while we are all working from home and afraid to turn on… Continue reading Recovery Fatigue and the Disaster Lady 2.0
5 Security Tips for Working Remotely
COVID-19 has dramatically changed how we do our jobs. Offices are shut down and working remotely is the new normal. Our business continuity planners at Assura thought it might be a good time to share some tips on safely working from home to keep you up and running while protecting your data. Reference these practices… Continue reading 5 Security Tips for Working Remotely
Coronavirus Response: Ensuring Delivery of Services!
To Our Valued Clients and Partners: I am reaching out to you to update you on Assura’s response to the Coronavirus (COVID-19) and our efforts to ensure that there are no interruptions of service for our clients. As continuity planning is one of our core services and one of our core values is “Eat Our… Continue reading Coronavirus Response: Ensuring Delivery of Services!
Send me money! I’ve been kidnapped!
After receiving a question from a client about a recent scam email, we thought it would be appropriate to address the topic of the “Nigerian Prince”, “Spanish Prisoner” or “419” letter and why it is still relevant in 2020. The type of fraud employed in these scams is known as an “advance-fee scam”. The scam… Continue reading Send me money! I’ve been kidnapped!
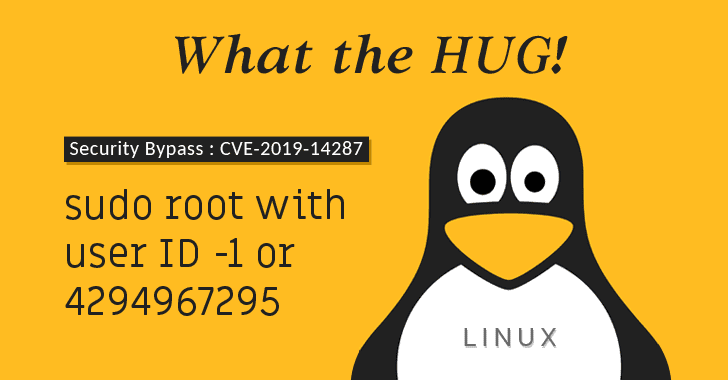
Vulnerability in Linux “sudo” Command Permits Anyone to Run Commands as Root
OVERVIEW Yesterday (October 14, 2019), a vulnerability was disclosed in the Linux Sudo command (CVE-2019-14287) that permits any user to execute commands as root (the Linux superuser). A very good full analysis of the flaw and how to exploit it is located at https://thehackernews.com/2019/10/linux-sudo-run-as-root-flaw.html. Assura’s Take This is an easy one: update Linux systems so that it uses… Continue reading Vulnerability in Linux “sudo” Command Permits Anyone to Run Commands as Root
The recent Capital One breach has everybody wondering if they are next…
The recent Capital One breach has everybody wondering if they are next. The simple answer is most likely – Yes – if you do nothing to protect yourself. Local counties and cities are a top target for cybercrime in the U.S. right now, and even the smallest locality can be a target. Just look at… Continue reading The recent Capital One breach has everybody wondering if they are next…
The Decision to Build or Buy a Cyber Security Capability
This is part 2 of a series to teach small-to-mid-sized organizations how to navigate the complex world of cyber security, how to budget, plan for, and implement a cyber security program. This series will give you the tools to make the decisions needed that protects your reputation and your ability to do what you do… Continue reading The Decision to Build or Buy a Cyber Security Capability
What is a Penetration Test (in Plain English)?
Maybe you’ve been told you that your organization needs to conduct a Penetration Test. Maybe it’s your auditor that’s said it, maybe your IT folks are telling you that it’s needed, or maybe you are the IT director and you just don’t know what to ask for from a penetration testing provider. To use a… Continue reading What is a Penetration Test (in Plain English)?
You Don’t Have to Do Cyber Security
This is part 1 of a series to teach small-to-mid-sized organizations how to navigate the complex world of cyber security, how to budget, plan for, and implement a cyber security program. This series will give you the tools to make the decisions needed that protects your reputation and your ability to do what you do… Continue reading You Don’t Have to Do Cyber Security