Assura’s Virtual Information Security Officers (VISO) deliver a complete solution for both cybersecurity and compliance. Also referred to in the industry as Fractional Chief Information Security Officers (CISO), their expertise is an invaluable asset to our clients. Watch the video below to meet some of the VISO team as they give cybersecurity tips on topics… Continue reading Cybersecurity Tips from Assura’s VISO Bunch
Category: Blog
Cybercrime Victim Resources for Individuals
At Assura, we protect businesses and government organizations but know that anyone can be a cyberattack victim. Below are resources that we recommend in the unfortunate situation of a personal cyberattack (links known to work as of the date of publication): Federal Trade Commission ReportFraud Federal Trade Commission Identity Theft and Online Security Federal Trade… Continue reading Cybercrime Victim Resources for Individuals
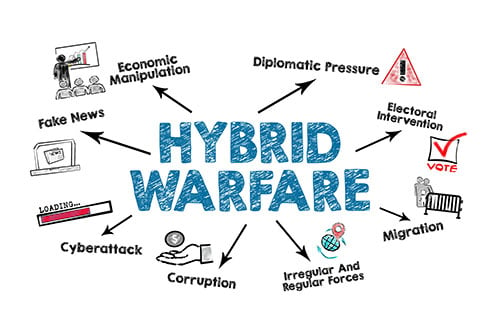
Thoughts on the Cyberwar Between Russia and Ukraine (and the Rest of the World)
In the early 2000s, I began to hear colleagues talk about cyber warfare and declare that the next battlefront wasn’t going to be fought with “boots on the ground” but in cyberspace. These statements had credibility because those saying this were retired high-level officers from the US armed forces. If anyone knew about the future… Continue reading Thoughts on the Cyberwar Between Russia and Ukraine (and the Rest of the World)
Fractional Information Security Officer: 3 Questions to Ask When Determining if Your Business Needs One.
Every week – if not every day, seemingly – an organization makes headlines for experiencing a cyber-attack. Sadly, for every Microsoft Exchange crisis, there are scores of small and medium-sized businesses (SMBs) wrestling with a data breach. While SMBs have been known to leverage fractional C-suite consultants for needs like accounting and HR, in the current… Continue reading Fractional Information Security Officer: 3 Questions to Ask When Determining if Your Business Needs One.
Cyber security means good business (opportunities, that is)
We like to think cyber security is good for business, well, because it’s our business. But we’ve had clients come to us looking to bolster their cyber security compliance and know-how, all in an effort to win more business on their end. Here are three ways you can leverage your cyber security strategy into your… Continue reading Cyber security means good business (opportunities, that is)
Assura is now a Cybersecurity Maturity Model Certification Registered Provider Organization
If you’re a DoD contractor or subcontractor, you’ve probably already been introduced to the Cybersecurity Maturity Model Certification but have you done anything about it yet? Well, we have good news because Assura is now a Cybersecurity Maturity Model Certification (CMMC) Registered Provider Organization (RPO). Total mandated compliance with CMMC is still on the horizon, but… Continue reading Assura is now a Cybersecurity Maturity Model Certification Registered Provider Organization
Zero Trust Principles — The Identity is Your New Network Perimeter
The world changed significantly over the last year. The pandemic forcefully launched many organizations into a proof-of-concept for remote work that some were not prepared for. With this change in the way we are all operating, the concept of zero trust is now making a strong resurgence in conversations around security architecture. What is Zero… Continue reading Zero Trust Principles — The Identity is Your New Network Perimeter
10 Cyber Security Steps to Better Protect Your Organization in 2021
Cyber security is a growing concern for every organization in every industry. Already, many experts predict cyber-attacks like phishing schemes and ransomware to significantly increase in 2021. As devastating as these attacks can be, there are a number of safeguards you can implement to better protect your organization. Here are 10 of the most effective… Continue reading 10 Cyber Security Steps to Better Protect Your Organization in 2021
There’s a Big Difference Between Good and Bad Cyber Security Training
Good cyber security training is a foundational aspect of any successful cyber security program. According to recent reports, more than 40% of data security breaches are the result of employee negligence. This can include unknowingly clicking on a phishing link or leaving sensitive information up on an unmonitored computer. This is why so many cyber security compliance… Continue reading There’s a Big Difference Between Good and Bad Cyber Security Training
Considerations When Developing a Cyber Security Budget
In many respects, a cyber security program with insufficient budget is like a car without enough gas to reach its destination. Not only will you not get where you need to go, when you eventually break down, you’ll find yourself in a particularly vulnerable spot. Your organization’s cyber security program is only as good as… Continue reading Considerations When Developing a Cyber Security Budget