Stay up to date with all the latest insights, news, perspective, and more.
Unmasked Podcast

Podcast Episode 21: Interview with the University of Richmond’s CTF Winning Team
What happens when passion, talent, and opportunity collide in the university's tech scene? Meet David Nathanson and Daniel Garay, the freshmen duo who took the University of Richmond's Capture the Flag (CTF) competition by storm. With Daniel bringing his coding journey from Nicaragua and David harnessing his
Categories
Cyber Heads-up

Phishing Campaign Installs Backdoor-Loaded VM to Evade Antivirus and Harvest Credentials
Overview Assura, Inc. has been made aware of this attack pattern, has taken steps to detect it in our managed services, and is following the attack in the blogs of security researchers who found this campaign. A recent phishing attack campaign has attackers installing a virtual
Unmasked Podcast

Podcast Episode 20: Interview with Alan Delahunty, his role as Vice President/Commercial Lines Agent
Unlock the secrets to navigating the ever-evolving world of cybersecurity and commercial insurance with expert insights from Alan Delahunty of McGriff Insurance. Discover how the complexity of cyber threats is reshaping insurance policies and learn why multi-factor authentication and other security measures are now industry standards.
Unmasked Podcast

Podcast Episode 19: Interview with Bill McInnis from Nucleus Security
Unlock the secrets to revolutionizing your cybersecurity strategy with insights from Bill McInnis of Nucleus Security. Journey through Bill’s extensive career, spanning over two decades and multiple sectors including email security and threat intelligence, and learn how he spearheaded groundbreaking changes since joining Nucleus in 2021.
Blog

Unify & Conquer: How Open XDR Streamlines Your Security Operations
In today's rapidly evolving cybersecurity landscape, staying ahead of threats requires innovation, agility, and robust partnerships. At Assura, we're dedicated to providing our clients with the most advanced and effective cybersecurity solutions. That’s why we are thrilled to announce our latest collaboration with Stellar Cyber, leveraging
Unmasked Podcast

Podcast Episode 18: From Application Developer to CEO: Greg Samuels on Entrepreneurial Success and Cybersecurity Priorities
Have you ever wondered what it takes to transition from a routine job to leading a successful company? Join us for a compelling conversation with Greg Samuels, CEO of Solvaria, as he shares his extraordinary journey from an application developer at Circuit City to founding his
News & Announcements

Assura, Inc Makes the Inc. 5000 Again for the 4th Year; Coming in at No. 2594!!
Assura Makes Inc. 5000 for the 4th time with three-year revenue growth of 44 percent! RICHMOND, Va., Aug. 13, 2024 /PRNewswire-PRWeb/ -- For the 4th Time, Assura, Inc Makes the Inc. 5000, at No. 2594 in 2024, With Three-Year Revenue Growth of 44 Percent Inc. revealed today that Assura, Inc ranks
Unmasked Podcast

Podcast Episode 17: Innovative Marketing and AI: Insights from Will Melton
Ever wondered how a young entrepreneur juggles the fast-paced world of tech sales and the demands of higher education? Meet Will Melton, the dynamic CEO of Exponent 21, who shares his fascinating journey from childhood ventures to helming a thriving company by the age of 20.
Unmasked Podcast

Podcast Episode 16: From Marine Corps Veteran to Tech for Troops Advocate: Jack Raymondson’s Inspiring Journey
Introduction: Welcome Jack Raymondson, Business Development Manager with Tech for Troops, a non-partisan, non-discriminatory Veteran services organization. Jack talks about his background in service and how he got involved with T4T Background of Tech for Troops: Overview of Tech for Troops' mission and vision. Discuss the
Unmasked Podcast

Podcast Episode 15: From Air Force Veteran to Cybersecurity Leader: Insights from Dave Mizell
Curious about how a 23-year Air Force veteran transitions into a leading role in network security? Join us as we chat with Dave Mizell, the Managing Director of Defensive Cybersecurity at Assura, Inc. Cybersecurity. Dave opens up about his initial experiences in a Security Operations Center
Unmasked Podcast

Podcast Episode 14: University of Richmond’s Winning Strategies of an All-Female CTF Squad
Discover the thrill of victory and the fascinating challenges faced in the world of cybersecurity competitions with the Lovely Ladies, an all-female champion team from the University of Richmond. Maggie and Leah join us to share their journey through the Capture the Flag event, providing rare
Unmasked Podcast

Podcast Episode 13: Special Guest: Bryan Carnahan, Director of Governance, Risk and Compliance
Discover the ins and outs of cybersecurity compliance as Bryan Carnahan joins me, Paul Blacker, to dissect the transition to Virginia's SEC 530 standard, a critical move for state agencies and their vendors. As the March 31st deadline approaches, we reveal how falling behind can result
Unmasked Podcast

Podcast Episode 12: The Dual-Edged Sword of AI in Cybersecurity with Nick Berrie
Discover the transformative power of AI in cybersecurity as I, Paul Blacker, engage with Assura's Nick Berrie in a revealing conversation about the future of online safety. Be prepared to have your notions of AI challenged as we unravel its multifaceted role in both advancing and
Unmasked Podcast

Podcast Episode 11: Special Guest from RVATech, Nick Serfass, CEO
Get ready for a very special Unmasked. Joining us in this episode is Nick Serfass, CEO of RVATech. For those not in the Richmond area, RVATech is on a mission to ignite the growth of the technology sector, the success of technology companies, and the vibrancy
Cyber Heads-up

CISA Urgent Advisory: Exploitation of Unitronics programmable logic controllers (PLCs)
Overview The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory concerning the exploitation of Unitronics programmable logic controllers (PLCs) within the Water and Wastewater Systems (WWS) Sector. These critical systems manage various aspects of water treatment and distribution, and cyber threat actors have
Unmasked Podcast

Podcast Episode 10: New AI Safety Standards, Cyber Skills Gap, Experience VS. Certification
Join us for another riveting episode of Unmasked to close out November. Get ready to dive into recent cybersecurity events and hot topics. We dissect AI's use across multiple industries, examining how it's trained for specific tasks and discussing its limitations. And for those of you
Unmasked Podcast

Podcast Episode 9: Special Guests from the University of Richmond
Join us for this very special episode as we sit down with the IT and Security experts from the University of Richmond. John Craft (Director of Information Security), Keith McIntosh (Chief Information Officer), and Svetla Walsh (Information Security Analyst) discuss their upcoming Capture the Flag (CTF)
Unmasked Podcast

Podcast Episode 8: Brightpoint’s IT Spirit Week, Infrastructure Security, AI’s Limitations
Welcome to another captivating episode of Unmasked! Join us as we embark on a thrilling journey into the dynamic realm of cybersecurity, led by the always entertaining and insightful Paul Blacker and Mark Harvey. In this episode, we're excited to discuss Assura's involvement in Brightpoint Community
Unmasked Podcast

Podcast Episode 7: Special Guest Jon DiMaggio, Chief Security Strategist & Author
Ever wondered what it's like to infiltrate a ransomware gang? Well, you're about to find out. We're joined by Jon DiMaggio, Chief Security Strategist of Analyst1 and author of the Art of Cyberwarfare, who takes us on a thrilling journey into the perilous world of ransomware.
Unmasked Podcast

Podcast Episode 6: Breach Class-Action, Help Desk Trickery, and Sextortion Scams
Welcome back for episode six of Unmasked! This week, we take a deep dive into the headlines of September, providing you with valuable context and insights into the latest cybersecurity events. The reverberations of the MOVEit disaster are still keenly felt, and this time, they've led
Unmasked Podcast

Podcast Episode 5: Fake Ads, Insider Threats, and a Big Data Dump
In this thrilling episode of Unmasked, our cybersecurity superheroes plunge headfirst into the late August headlines to uncover the most cutting-edge and formidable cyberattacks. Fasten your seatbelts and ensure your hands remain securely inside the vehicle as we embark on an exhilarating journey through the world
Unmasked Podcast

Podcast Episode 4: Burger Breach, Extra Credential-Stuffing, with a Side-Channel
In the latest episode of Unmasked, we're taking a deep dive into August headlines, unpacking all the threats and vulnerabilities that lurk in our digital realm. We're covering some major ground, from the Burger King data breach to unsettling cyber attacks on hospital EMR systems. Join
Unmasked Podcast

Podcast Episode 3: Breaches, Scams, and Countdown to DEFCON
In this episode, we dive into the end of July headlines, covering a class action lawsuit against John Hopkins following a major data breach, emphasizing the need for better data handling and security practices. We also explore the complexities of IoT device regulation, questioning the absence
Unmasked Podcast

Podcast Episode 2: Summer Phishing Season is Hot, but so is DEFCON
Ever wondered how safe your digital life really is? Prepare to open your eyes to the unseen dangers lurking in your inbox and online transactions. Welcome to our latest episode of Unmasked, where the superheroes of cybersecurity provide a clearer understanding of the threats we face
Unmasked Podcast

Podcast Episode 1: Decoding the Dark Secrets of Cyberattacks
Assura is excited to release the first episode of our new podcast–Unmasked. Where the superheroes of cybersecurity provide a clearer understanding of the threats we face in our digital world. Unmasked is hosted by our very own in-house cybersecurity experts Paul Blacker and Mark Harvey. About
Cyber Heads-up

MOVEit Transfer Software: Critical Zero-day Being Actively Exploited
Overview Assura's Security Operations Center is seeing active exploitation of a SQL Injection flaw in Progress Software's MOVEit Transfer product first announced on May 31, 2023. The vulnerability is CVE-2023-34362. Technical Analysis A full technical analysis has been done by our friends at Huntress, who have
Cyber Heads-up

Critical Vulnerability in Zyxel Network Appliances Exploited, PoC Scripts Circulating
Overview A few days after Rapid7 posted their technical analysis of CVE-2023-28771, which included a proof-of-concept exploit, Assura's Offensive Security Operations team noticed a lot of chatter on social media and hacking forums regarding the exploitation of Zyxel network appliances. CVE-2023-28771 is a pre-authentication remote code
Case Study

An IT team of one quickly takes control of 400 vulnerabilities.
Download PDF CASE STUDY Challenge: Organizations are inundated with hundreds of thousands of vulnerabilities every year. After years of experience, we know most organizations can only patch about 1 in 10 (10%) vulnerabilities discovered in their environment based on resource capacity. This is simply insufficient to
Cyber Heads-up
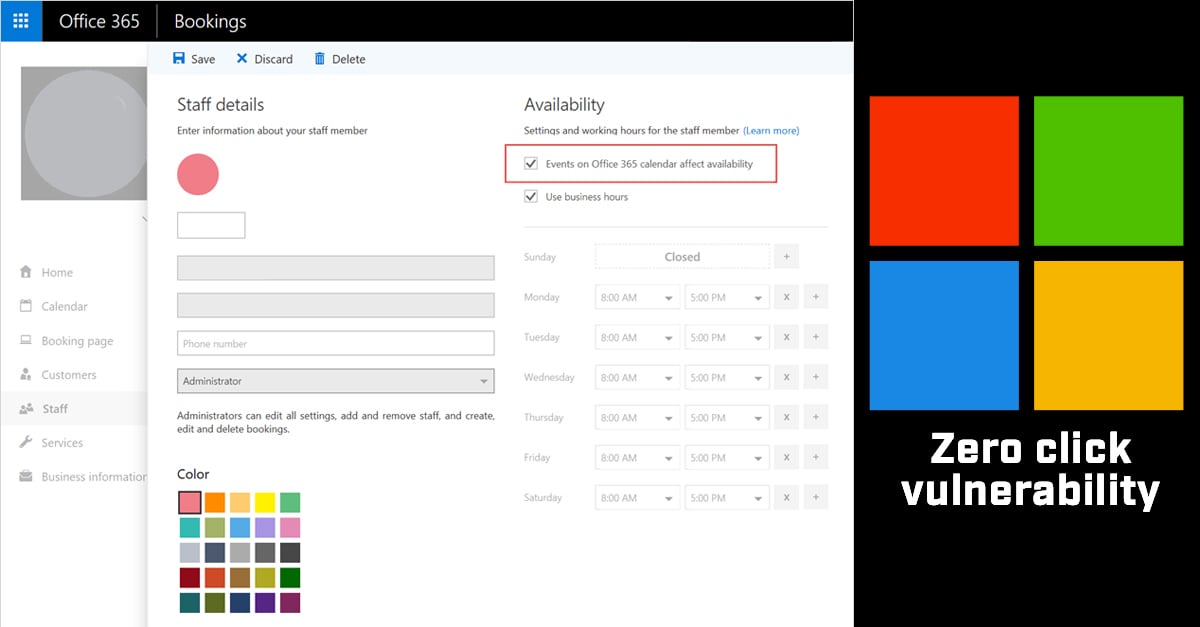
Exploiting CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
https://www.youtube.com/watch?v=zH7uhzLywYg Overview Assura’s Offensive Security Operations Team has been looking into MDSec’s Dominic Chell’s research into the recent Microsoft Office Outlook updates where Dominic found that there is a privilege escalation vulnerability within Outlook. Via this vulnerability, a remote attacker can create a malicious Outlook Appointment
Case Study

Virginia municipality discovers a dangerous backdoor
Challenge: With attacks on municipalities on the rise, a midsized county in Virginia knew it needed to improve its cybersecurity posture. The problem was they were not sure where to begin. So they enlisted our services to help them determine their strengths and vulnerabilities. Solution: Assura
Blog
Cybersecurity Tips from Assura’s VISO Bunch
Assura's Virtual Information Security Officers (VISO) deliver a complete solution for both cybersecurity and compliance. Also referred to in the industry as Fractional Chief Information Security Officers (CISO), their expertise is an invaluable asset to our clients. Watch the video below to meet some of the
News & Announcements
A Humorous LinkedIn “Celebrate an Occasion” Hack for Cybersecurity Awareness Month
For Cybersecurity Awareness Month, Assura wanted to grab the world’s attention and showcase cyber defense in a humorous and disruptive way. Humor is often a very powerful tool for communicating a serious message and we felt it was the way to go for this cybersecurity awareness
Cyber Heads-up

UPDATE: Take Immediate Action: Two New Microsoft Exchange Zero-Day Vulnerability confirmed by Microsoft
Overview This Cyber Heads-up has been updated to include a PowerShell command to determine whether an Exchange server has already been compromised. Assura’s Defensive Security Operations Center (SOC) is monitoring recently reported zero-day vulnerabilities in Microsoft Exchange 2013, 2016, and 2019 being exploited in the wild.
Cyber Heads-up

Apple announces an ‘actively exploited’ vulnerability that allows hackers to fully control devices
Overview On August 17, 2022, Apple announced a zero-day vulnerability that exploits a software weakness that affects both the kernel (CVE-2022-32894) and the WebKit on Apple devices (CVE-2022-32893). The kernel is a layer of the operating system common on all Apple devices, and the WebKit is
Blog

Cybercrime Victim Resources for Individuals
At Assura, we protect businesses and government organizations but know that anyone can be a cyberattack victim. Below are resources that we recommend in the unfortunate situation of a personal cyberattack (links known to work as of the date of publication): Federal Trade Commission ReportFraudFederal Trade
News & Announcements

Assura Announces Vulnerability Management-as-a-Service
Richmond, VA - Today, I am thrilled to announce the General Availability of Assura's Vulnerability Management-as-a-Service (VMaaS). Assura's VMaaS combines industry leading tools to identify and actively manage security weaknesses and insecure configurations in client environments. VMaaS is for organizations who want the power of industry
Blog

Assura’s Top 5 Misconceptions about Penetration Testing
https://www.youtube.com/embed/M_gMMORGYgc With the increasing number of organizations now seeking penetration testing due to regulatory requirements, more and more companies are claiming to offer a service that checks this box. Assura wanted to help clarify some of the top misconceptions you may encounter when searching for a
Cyber Heads-up

Follina Zero-day Exploit Permits Attackers Complete Takeover of Victim Systems Through Malicious Microsoft Office Documents
Overview of Follina On Friday, May 27th, 2022, @nao_sec announced on Twitter that they had discovered a novel attack technique utilized in a malicious document (maldoc) submitted from a Belarus IP address to VirusTotal. The new technique uses Microsoft’s Microsoft Support Diagnostic Tool (MSDT) to retrieve
Cyber Heads-up

CISA Releases Advisory About Multifactor Authentication Bypass with Duo — Duo Responds
TL;DR Russian state-sponsored attackers compromised an NGO by exploiting the weak credentials of an inactive user, default settings in the Duo multifactor authentication service, and PrintNightmare to take over the environment. The way to protect organizations is to implement good cyber hygiene and modifying a couple
Cyber Heads-up

UPDATE: NVIDIA Code Signing Certificates Compromised – Temporarily Halt Updates/Installation of NVIDIA Software
Update March 16, 2022: It’s been twelve days since we posted this Cyber Heads-up and this seems to have dropped out of the news and out of discussion. NVIDIA has been deafeningly silent about this. Our guidance remains the same. Make sure that your environment is
Cyber Heads-up

Assura Announces Discovery of Two Vulnerabilities in Quicklert for Digium Switchvox
TL;DR Today Assura is announcing the discovery of two new vulnerabilities in Quicklert for Digium Switchvox. Late in 2021, Assura’s Offensive Security Operations team conducted a penetration test that uncovered two critical severity vulnerabilities in Quicklert for Digium Switchvox Version 10 Build 1043 resulting in two new CVEs, discussed
Blog
Thoughts on the Cyberwar Between Russia and Ukraine (and the Rest of the World)
In the early 2000s, I began to hear colleagues talk about cyber warfare and declare that the next battlefront wasn’t going to be fought with “boots on the ground” but in cyberspace. These statements had credibility because those saying this were retired high-level officers from the
Cyber Heads-up

Assura Continues to Recommend Operation in a “Shields Up” Defensive Posture
TL;DR Earlier in February, the Cybersecurity and Infrastructure Security Agency (CISA) issued a “Shields Up” warning advising American companies to be extra cautious about potential hacking attempts from Russia as tensions with the country rise, particularly during the Russia-Ukraine crisis. As the situation since the invasion of Ukraine
Cyber Heads-up

Cisco Issues Field Notice to Firepower Customers – May Lose Talos Security Intelligence Updates
TL;DR Cisco issued a Field Notice on February 21, 2022 warning customers of its FirePOWER Services Software for ASA, FirePOWER Threat Defense (FTD) Software, and Firepower Management Center Software that the root certificate that signed the TLS certificate for security intelligence updates by its Talos group
Cyber Heads-up
Highly Effective Russian Phishing Campaigns Against Ukraine May Pivot to U.S. Targets
TL;DR Russian state sponsored threat actors are using malicious Microsoft Office documents with remote macros to compromise Ukrainian targets. With tensions between Russia and Ukraine at a boiling point, we would not be surprised if these attacks to pivot to U.S. targets in critical sectors once
Case Study

Protecting a university’s network against both hackers and a student workforce.
Challenge: A university approached Assura with a need to meet all the necessary regulatory requirements, including Commonwealth of Virginia cybersecurity standards, PCI DSS, FERPA, and HIPAA. In addition, they had a unique challenge that most other organizations don’t have. Because they employ students to help run
Case Study

ProDefense™ XDR: Quickly secures a global company’s all-new virtual call center.
Challenge: A U.S. government contractor tapped a global company that specialized in workforce mobilization and staffing to create and staff a call center. Typically, this would not have been a significant challenge. However, this happened at the peak of the COVID-19 global pandemic, which meant the
Case Study

Delivering election security for 11 Virginia localities in a single coordinated effort.
Challenge: The Federal Emergency Management Agency (FEMA) challenged the state of Virginia with helping to secure elections. A part of this challenge was making government localities cyber secure as well. FEMA offered a grant to help small localities achieve the level of security required. Eleven government
Cyber Heads-up

Update 2: Severe Zero-Day Vulnerability in Apache Log4j Package Hits the World
December 20, 2021: A new Denial of Service vulnerability was announced over the weekend by The Apache Foundation. They now recommend that software vendors and IT departments use version 2.17.0. This means that systems that were patched as of Friday, December 17, 2021 may need to
Cyber Heads-up

TrojanSource – Why The Threat Is Real But The World Isn’t On Fire
Overview Recently, researchers at the University of Cambridge published a paper detailing how obfuscation techniques can be used to inject malicious code into source code prior to compilation. Depending on the compiler, the malicious source code would be hidden from the user’s view, yet still successfully
Blog

Fractional Information Security Officer: 3 Questions to Ask When Determining if Your Business Needs One.
Every week – if not every day, seemingly – an organization makes headlines for experiencing a cyber-attack. Sadly, for every Microsoft Exchange crisis, there are scores of small and medium-sized businesses (SMBs) wrestling with a data breach. While SMBs have been known to leverage fractional C-suite consultants
Cyber Heads-up

I do not like HiveNightmare, SeriousSam. I do not like it here or there. I do not like it anywhere!
TL;DR No, it’s not a new Dr. Seuss story – it’s a recently discovered zero-day exploit (CVE-2021-36934, known as HiveNightmare or SeriousSam) that allows an attacker to read the contents of a Security Account Manager (SAM) file on Windows 10 and 11 systems with non-administrator user
Blog

Cyber security means good business (opportunities, that is)
We like to think cyber security is good for business, well, because it’s our business. But we’ve had clients come to us looking to bolster their cyber security compliance and know-how, all in an effort to win more business on their end. Here are three ways
Cyber Heads-up

Windows Print Spooler “PrintNightmare” Vulnerability, Exploits
TL;DR There is a Windows vulnerability that uses Print Spooler to gain remote code execution on devices. In the Assura’s Take section, we offer three mitigation options: 1. Disable the print spooler service, 2. Apply an ACL to restrict print driver installation/upgrades. 3. Disable remote connections
Cyber Heads-up

Kaseya’s VSA Supply Chain Ransomware
TL;DR A supply chain exploit of Kaseya’s VSA Remote Management service puts customers of managed service providers (MSPs) using this tool at risk of REvil ransomware. Assura recommends anyone using Kaseya VSA to follow Kaseya guidance on server hardening when available, and also download and run
Blog

Assura is now a Cybersecurity Maturity Model Certification Registered Provider Organization
If you’re a DoD contractor or subcontractor, you’ve probably already been introduced to the Cybersecurity Maturity Model Certification but have you done anything about it yet? Well, we have good news because Assura is now a Cybersecurity Maturity Model Certification (CMMC) Registered Provider Organization (RPO). Total mandated
Cyber Heads-up

Verkada Cameras Hacked and New Microsoft DNS Server Vulnerability
It’s been quite a few months in the cyber security world, and last week was no exception with two major vulnerabilities concerning Verkada cameras and Windows DNS servers. Both vulnerabilities are unpacked in the below CHU alerts! Alert 1: Verkada Cameras Hacked, Leads to Network Compromise
Cyber Heads-up

Update to HAFNIUM/Microsoft Exchange Server zero-day vulnerabilities
Overview On March 4, 2021 we posted a Cyber Heads-Up article titled, “Chinese State-Sponsored Group HAFNIUM Exploiting Exchange Zero-Day Vulnerabilities – PATCH NOW”. Today, we are revisiting this attack campaign with updates about what Assura and other security firms are seeing during response efforts. If you
Cyber Heads-up

Chinese State Sponsored Group HAFNIUM Exploiting Exchange Zero-Day Vulnerabilities – PATCH NOW
Overview Microsoft recently released out-of-band security updates to address four new vulnerabilities in Exchange Server (on-premises). The series of exploits is actively being used by malicious actors to steal emails and compromise internal networks. What Do We Know About This Attack? The Microsoft announcement contains four new vulnerabilities,
Blog
Zero Trust Principles — The Identity is Your New Network Perimeter
The world changed significantly over the last year. The pandemic forcefully launched many organizations into a proof-of-concept for remote work that some were not prepared for. With this change in the way we are all operating, the concept of zero trust is now making a strong
Blog

10 Cyber Security Steps to Better Protect Your Organization in 2021
Cyber security is a growing concern for every organization in every industry. Already, many experts predict cyber-attacks like phishing schemes and ransomware to significantly increase in 2021. As devastating as these attacks can be, there are a number of safeguards you can implement to better protect
Cyber Heads-up

Oversharing in the Age of COVID-19
To say that selfies have been popular for the last two decades would be an understatement. Everyone from celebrities to grandparents have been posting pictures online. In the Age of Covid, the posting of your Covid-19 vaccine record is just the latest selfie phenomenon. However, this
Cyber Heads-up

CISA Announces Active Exploitation of SolarWinds Orion Platform – What You Should Know
Overview The Cybersecurity and Infrastructure Security Agency (CISA) released an alert regarding the active exploitation of the SolarWinds Orion platform. It was found by FireEye that SolarWinds Orion versions 2019.4 through 2020.2.1, released between March 2020 and June 2020, were compromised in a supply chain attack. What
Cyber Heads-up

Cyber Security Firm FireEye Reports Major Breach, Assura’s response and monitoring plan
Overview Major news shocked the cyber security world yesterday (Tuesday, December 8) when FireEye, the parent company of Mandiant, announced they had been breached and their Red Team tools were stolen. Everyone can be breached, and we mean everyone. FireEye’s Mandiant division is the company everyone runs to
Blog

There’s a Big Difference Between Good and Bad Cyber Security Training
Good cyber security training is a foundational aspect of any successful cyber security program. According to recent reports, more than 40% of data security breaches are the result of employee negligence. This can include unknowingly clicking on a phishing link or leaving sensitive information up on an unmonitored
Blog

The Difference Between an MSP and an MSSP: The Extra “S” Really Does Make a Difference!
Now that Turkey Day is done and we are waiting for a COVID-free Santa to visit our homes (because surviving quarantine should put us all on Santa’s Nice List), it’s time to answer a common question I receive this time of year. As people prepare their 2021 budgets
Blog

Considerations When Developing a Cyber Security Budget
In many respects, a cyber security program with insufficient budget is like a car without enough gas to reach its destination. Not only will you not get where you need to go, when you eventually break down, you’ll find yourself in a particularly vulnerable spot. Your
Cyber Heads-up

A Busy Week in Cyber Threats
Key Takeaways It’s been a busy several days in cybersecurity. Below is an overview of the key events, followed by Assura’s take on these matters. Google announced the discovery of a zero-day privilege escalation flaw in Microsoft Windows, possibly dating back to Windows 7.The U.S. Department
Cyber Heads-up

Don’t You Be My Neighbor – Specially Crafted IPv6 Packet Causes Blue Screen of Death
Overview: On October 13, US-CERT and US Cyber Command issued a Tweet urging organizations and users to install updates released as part of Microsoft’s “Patch Tuesday” security and feature updates. This round of patches closes a particularly nasty vulnerability where a specially crafted IPv6 packet can
Blog

New State Mandated COVID Guidelines for Virginia Business
♪♫ “Hello DOLI! Well, hello DOLI! It’s so nice to have you back where you belong.” ♬♩ Not the Carol Channing Broadway version you were expecting, was it? This week’s post is on the new Virginia Department of Labor and Industry (DOLI) emergency standard that focuses
Disaster Lady Q&A

Cyber Hygiene: Is there funk up all in your business?
When you talk to your team about cyber security, do you get that not-so-fresh feeling?When you have a date with your executives or stakeholders, are you afraid of things going too far and that they might find out that your business isn’t clean? If so, it’s
Cyber Heads-up

A vulnerability called “SIGRed” (CVE-2020-1350), exploits a buffer overflow within the way that Windows DNS Servers process SIG resource record types.
Recently, Check Point researcher Sagi Tzadik published a blog post announcing a new attack against Windows DNS Servers which can allow an attacker to create Denial-of-Service conditions and possibly gain Domain Administrator access. What makes this specific vulnerability unique is that it isn’t really new it has been around for 17 years
Disaster Lady Q&A

The top 3 things you should make sure you are doing to protect your company today!
The pandemic has changed the way that we will operate our companies forever. In a Gallup Poll taken in the week of March 30 – April 2 of this year, sixty-two percent of employed Americans currently say they have worked from home during the crisis. That number was
Blog

Love Gloves and Zorro
Several localities around the United States have moved into the first phase of reopening their economies and trying to get to what we will begin to know as our new normal. My stylist has over 200 appointments that she needs to catch up on and people
Disaster Lady Q&A

To Pay, or Not to Pay, That is the Question.
New PPP Loan Forgiveness Guidelines Broken Down There are many businesses out there that have either received Paycheck Protection Program (PPP) loans during the first round of funding for the CARES Act or are slated to receive it during the second round. As mentioned in my previous
Cyber Heads-up
Dark Web Intelligence Firm Reports New Attacks Against Zoom Users
Overview Staying with the recent theme of attacks on the work from home model, we’re back with another warning about Zoom. It’s not that we have anything against Zoom, but the platform rapidly became part of the cultural lexicon over the last couple of months due
Blog

Intimate Love in the Time of Quarantine: Love during a disaster.
There was a movie in 2007 called Love in the Time of Cholera. It starred a young Javier Bardem as a man who falls in love with a girl after seeing her through a shop window. It takes place during the Plague Year (as they called
Cyber Heads-up

Attack Against Azure AD Pass-Through Authentication Agent can Compromise Azure/Office 365 Tenants
Overview Recently, Varonis researcher Eric Saraga published a blog post announcing a new attack against Azure Active Directory (Azure AD) which can allow an attacker to log in as any synchronized user. The attack method exploits a flaw in the Pass-Through Authentication (PTA) password verification method of allowing
Disaster Lady Q&A

Part 2 of “Is your baby ugly?” Getting lean without cutting bone!
If you haven’t read Part 1, click here. Believe it or not, there is one blessing out of the disaster that is COVID-19. It provides business leaders with the opportunity to take a moment, step back, look at the long term viability of our business, and take
Disaster Lady Q&A

I applied for federal loan assistance and learned that the funds have been exhausted. What do I do?
Question to the DL: I own two environmental companies. Both firms have zero revenue and mounting expenses especially now due to shut down caused from COVID-19. I applied for federal loan assistance and learned that the funds have been exhausted. The environmental practice was already on its
Disaster Lady Q&A

Is Your Baby Ugly? Staying Agile During a Disaster
Years ago, when I started out with my first company, one of the best pieces of advice I received was to always make sure you could tell if your baby was ugly. Now, that doesn’t mean our human or fur babies (because those babies are cute
Disaster Lady Q&A

Tracking Time and Work Productivity
Question to the DL: I found that users that have a dedicated space and get dressed as though they are going to work and have set work times are most productive and have the right mindset compared to someone trying to work in their PJs in
Disaster Lady Q&A

About the SBA’s Economic Injury Disaster Loan Program
Question to the DL: Strategies to access the new SBA loans for a startup during a disaster? Disaster Lady Answer: Ah, our old friends at the SBA (Small Business Administration). For many of us, we wouldn’t have a business unless we occasionally used SBA backed loans.
Disaster Lady Q&A

IT Disaster Recovery Plans On The Fly
Question to the DL: Do you have a DR template we can use? Disaster Lady Answer: I do have different templates, but there is a reason that you do not see planners that just post templates out there. It is because there are different types of
Disaster Lady Q&A

How To Handle Price Changes During a Disaster
Question to the DL: What pricing advice do you have for MSPs that are suddenly asked/expected to get their clients enabled for remote work from home? Disaster Lady Answer: When it comes to pricing strategies, you need to be careful. It is appropriate to build an extra
Blog

SBA’s Paycheck Protection Loan Program and the CARES Act
On Friday, the Small Business Administration (SBA) posted the final application for the Paycheck Protection Program for small businesses. This is the result of the Coronavirus Aid, Relief, and Economic Security (CARES) Act, a bill that was fast-tracked through Congress and signed by the President, part
Cyber Heads-up

Hackers Exploiting the Introduction of Video-Teleconferencing into Your Environment
Overview With most employers shifting to a work from home (WFH) model attackers are chomping at the bit to exploit the introduction of video-teleconferencing (VTC) into your environment. VTC programs such as Zoom, GoToMeeting, or Microsoft Teams are not anything new and neither are their exploitation
Disaster Lady Q&A
Is COVID-19 airborne?
Question to the DL: I have heard of experts saying both sides of this – is the virus airborne or not? In the interview I saw of Michael Osterholm – I believe he said it was air born – not simply a virus on something. I
Blog

Recovery Fatigue and the Disaster Lady 2.0
Hey folks! This has been quite a week. New COVID scams from hackers saying they have the cure to Dr. Fauci. Researchers announcing they are puzzled and don’t know why some folks get sick, while others just have mild symptoms. All of this while we are
Disaster Lady Q&A

Businesses Finding Medical Supplies
Question to the DL: I have TP in my warehouse but I am looking for sources for isolation gowns. Disaster Lady Answer: If you really are looking for sources, the best thing for you to do would be to sign up with a Group Purchasing Organization like
Disaster Lady Q&A

About Business Interruption Insurance
Question to the DL: What about my business insurance? Disaster Lady Answer: There are two truths about business insurance and major disasters that you need to know: Truth 1: Insurance companies do not make their money by paying out claims. Do not expect that you will
Cyber Heads-up

New Phishing Attack Tells Recipient They May Have Contracted COVID-19
Overview As the world continues to face the COVID-19 pandemic, attackers are preying on our fears more than ever. There is no depth to which cybercriminals will not sink, even in the case of a worldwide crisis. It’s unfortunate, but some people just want to watch
Disaster Lady Q&A

Business Finance During Disasters
Question to the DL: How do I manage finances when I do not have a CFO? Disaster Lady Answer: This is a tough one, but the head of an organization has to be actively managing the finances per day. If you do not have a CFO, there
Disaster Lady Q&A

What do you do when Face-to-Face Selling is no Longer an Option?
Question to the DL: Since this whole COVID broke, my whole business has slowed down. A face-to-face conversation was the best way for us to get new customers which is not possible right now. What do we do? Disaster Lady Answer: The easy answer to the question
Disaster Lady Q&A

After the First 72 Hours – What’s Next?
Question to the DL: I had a great emergency response with hand sanitizers and cleaning the office. Is that enough? What’s next. Disaster Lady Answer: This is going to be a hard answer to give you, but you need to hear it. The beginning/last week was the
Disaster Lady Q&A

Dealing With Uncertainty During Disasters
Question to the DL: What do I tell my employees about their jobs? I don’t know if they are going to have one in the upcoming weeks. Disaster Lady Answer: You have to balance your messages. Don’t lie or bullsh*t people. They know when you are doing
Disaster Lady Q&A

To Telework or Not To Telework
Question for the DL: I haven’t even started to respond and am trying to figure out what is going on. My folks are still coming into work. What do I do? Disaster Lady Answer: Your employees are your first priority. If you take them for granted
Blog

5 Security Tips for Working Remotely
COVID-19 has dramatically changed how we do our jobs. Offices are shut down and working remotely is the new normal. Our business continuity planners at Assura thought it might be a good time to share some tips on safely working from home to keep you up
News & Announcements

Coronavirus Response: Ensuring Delivery of Services!
To Our Valued Clients and Partners: I am reaching out to you to update you on Assura’s response to the Coronavirus (COVID-19) and our efforts to ensure that there are no interruptions of service for our clients. As continuity planning is one of our core services
Disaster Lady Q&A

About The Disaster Lady
Hello all. I have never done something like this before, but we are in unusual times and that calls for unusual approaches to things. I am writing as a certified disaster recovery planner to help you figure out how to get through these extreme circumstances. Let’s
Cyber Heads-up

Cisco Smart Install Feature Still Poses Significant Security Vulnerability
Overview Assura does a significant amount of penetration tests for our clients and we like to communicate the trends that we see as we do these. During the last three, we’ve seen a recurring severe configuration vulnerability using the Smart Install feature of devices running Cisco’s IOS and
Cyber Heads-up
PATCH NOW: Two Severe Vulnerabilities in Microsoft’s First “Patch Tuesday” of 2020
Overview If you haven’t already heard about these in the press, we’re here to tell you about them. On Tuesday of this week (14 January 2020), the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) released advisory number AA20-014A: Critical Vulnerabilities in Microsoft Windows
News & Announcements

Assura Named one of the Top 10 Most Promising Cybersecurity Consulting/Service Companies of 2019 by CIO Review Magazine
We are very proud to announce that CIO Review magazine named Assura as one of the top 10 most promising cybersecurity consulting/service Companies of 2019! In 2020, cyber attacks are commonplace, sophisticated, and severe and cyber security now has to be a core component of business
Cyber Heads-up

Today is the Day that Windows 7 and Server 2008/r2 Security Updates End
Overview If you’re in IT (and haven’t been living under a rock), you know that today is the day that Microsoft officially ends extended support for Windows 7, Windows Server 2008, and Windows Server 2008R2. We went through this back in April of 2014 and July
Cyber Heads-up

Iranian Espionage/Cyber Warfare Threat Briefing
Overview Our friends and partners at Dark Web intelligence firm IntSights have an excellent (and relatively short) threat briefing about Iranian cyber threat actors and the tactics they use for cyber espionage and warfare. The briefing includes recommendations for mitigation of these threats. The briefing can be downloaded
Blog
Send me money! I’ve been kidnapped!
After receiving a question from a client about a recent scam email, we thought it would be appropriate to address the topic of the “Nigerian Prince”, “Spanish Prisoner” or “419” letter and why it is still relevant in 2020. The type of fraud employed in these
Cyber Heads-up

DHS Releases Alert for Potential Iranian Cyber Attacks in Response to U.S. Military Strike in Baghdad
Overview On Monday, January 6, 2020, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) released Alert AA20-006A, warning about potential cyberattacks on U.S. companies by the nation of Iran. The alert includes an overview of the threat profile of Iranian state-sponsored offensive
News & Announcements

Assura Announces Ransomware Protection Pack™
I am thrilled to announce the general availability of Assura’s Ransomware Protection Pack™, a comprehensive suite of tools and services that protects organizations of all sizes from falling victim to the scourge of ransomware. Ransomware is a type of malicious software that encrypts data on computers
Cyber Heads-up
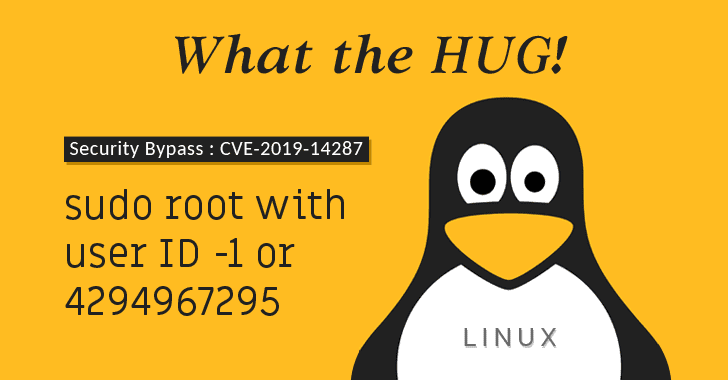
Vulnerability in Linux “sudo” Command Permits Anyone to Run Commands as Root
OVERVIEW Yesterday (October 14, 2019), a vulnerability was disclosed in the Linux Sudo command (CVE-2019-14287) that permits any user to execute commands as root (the Linux superuser). A very good full analysis of the flaw and how to exploit it is located at https://thehackernews.com/2019/10/linux-sudo-run-as-root-flaw.html. Assura’s Take This is an
Blog

The recent Capital One breach has everybody wondering if they are next…
The recent Capital One breach has everybody wondering if they are next. The simple answer is most likely – Yes – if you do nothing to protect yourself. Local counties and cities are a top target for cybercrime in the U.S. right now, and even the
Cyber Heads-up

New Major Flaw Found in Intel and (Possibly) AMD Processors
Good afternoon - Overview Last night US-CERT (the Department of Homeland Security’s Computer Emergency Response Team) announced the public disclosure by researchers at endpoint security protection company Bitdefender of a new CPU-level information compromise vulnerability. Dubbed “SWAPGS”, the vulnerability is used to execute a “side channel”
News & Announcements

Assura Named 2019 Top SIEM Solution Provider
We are very proud to announce that Assura has been named one of the top 10 SIEM solution providers for 2019 by Enterprise Security Magazine! Security information and event management (SIEM) is key to creating a good threat detection and monitoring system for your business. Good
Cyber Heads-up

Cyber Heads-Up: Week of July 29th
Good morning! This week, we’ve got a doozie for you. As usual, the bad guys are busy trying to find their next way into a system they don’t belong in. Read on to find out more about them, and our take on what exactly is going
Cyber Heads-up

Beware Amazon Prime Day Scams
Good morning- Overview Today (Monday, July 15, 2019) marks the start of Amazon Prime Day. Prime Day, which runs through tomorrow is a once-a-year event where Amazon.com places numerous items on sale at steep discounts. It is also a “prime” opportunity for scammers to send phishing
Cyber Heads-up

Cyber Heads-up: Week of May 20, 2019
Good morning- Last week was a very active week in the world of cyber threats. Hacked antivirus software vendors, Microsoft’s unusual release of a security patch for Windows XP, Linux Kernel zero-day, WhatsApp being used to deliver spyware, Google issuing a recall on its Titan security
Cyber Heads-up

New MegaCortex Ransomware Leverages Existing Malware Infections
Good morning- Overview Sophos is reporting a sudden spike in a ransomware strain that it disclosed back in March of this year. Dubbed “MegaCortex”, the ransomware appears to be injected through the Emotet and Qbot (aka Qakbot) malware. Both of these malware families have the ability
Cyber Heads-up

Assura Awarded IT Security Contract with Metropolitan Washington Airports Authority
I am proud to announce that the Metropolitan Washington Airports Authority (MWAA) has awarded contract SC-18-01022 to Assura for IT Security services. The contract provides the Authority, which operates Washington Dulles International Airport (KAID), Reagan National Airport (KDCA), and the Dulles Toll Road with access to Assura’s wide range of expert cyber
News & Announcements

Assura Awarded VASCUPP Contract for Cyber Services
Hi everyone! We’re delighted to announce that Assura was just awarded a contract for cyber security products and services by the Virginia Association of State College and University Purchasing Professionals (VASCUPP). Contract number UCPJMU5318 allows eligible purchasing activities to procure cyber security-related products and services from Assura at pre-negotiated
Blog

The Decision to Build or Buy a Cyber Security Capability
This is part 2 of a series to teach small-to-mid-sized organizations how to navigate the complex world of cyber security, how to budget, plan for, and implement a cyber security program. This series will give you the tools to make the decisions needed that protects your
Blog

What is a Penetration Test (in Plain English)?
Maybe you’ve been told you that your organization needs to conduct a Penetration Test. Maybe it’s your auditor that’s said it, maybe your IT folks are telling you that it’s needed, or maybe you are the IT director and you just don’t know what to ask
Blog

You Don’t Have to Do Cyber Security
This is part 1 of a series to teach small-to-mid-sized organizations how to navigate the complex world of cyber security, how to budget, plan for, and implement a cyber security program. This series will give you the tools to make the decisions needed that protects your
Blog
Logos and Branding and Websites, Oh My!
Welcome to Assura’s new presence on the web! New logo, new brand, new web design, new Internet domain, and a move of our headquarters to a new location. Whew! And that’s just the stuff you can see! This marks a major milestone in our company’s history because
Blog

The Duel Factor Podcast – Coming Soon (We Promise!)
CEO and CTO. Husband and Wife. Welcome to Assura’s Cybersecurity Podcast hosted by Karen and Joshua Cole! Coming soon!
Blog

The Dark Web
The Surface Web is only 10% of the total size of the Internet. All sites on the surface web are indexed by search engines and are easily accessible. Examples of the surface web are Facebook, Twitter, YouTube, etc. The Deep Web and Dark Web contain the
