Overview
A few days after Rapid7 posted their technical analysis of CVE-2023-28771, which included a proof-of-concept exploit, Assura’s Offensive Security Operations team noticed a lot of chatter on social media and hacking forums regarding the exploitation of Zyxel network appliances. CVE-2023-28771 is a pre-authentication remote code execution vulnerability affecting the WAN interfaces of several Zyxel network appliances, including their ATP, USG FLEX, VPN, and ZyWALL/USG. Pre-authentication remote code execution vulnerabilities tend to be the worst types of vulnerabilities when exploitable because it often allows adversaries to take over devices with little to no barrier to entry. Luckily, Zyxel has already put out an advisory and provided patches for this vulnerability, originally discovered by TRAPA Security.
Technical Analysis
Within Zyxel’s 4.60 firmware, originally released in October of 2020, there is a vulnerability that allows an unauthenticated attacker to send a specially crafted Internet Key Exchange (IKE) packet to the Zyxel appliance’s IKE packet decoder on the WAN interface and obtain remote code execution as the root (highest privilege) user.
Patch diffing is a common tactic for security researchers and adversaries to determine where a vulnerable component of a product is in previous versions. By determining where changes in code occurred, they can often determine how and why the code changed to reverse engineer the vulnerability and craft a proof-of-concept exploit. This is what Rapid7’s team did.
By diffing the vulnerable and patched versions of the Zyxel firmware, Rapid7 was able to determine that the binary/sbin/sshipsecpm was the vulnerable component. This component was being used to write a client (adversary) supplied error message to a log file by constructing a system command which was then executed by a call to the system to perform the action.
Once decompiled, Rapid7 was able to see that there was a variadic function within ssh_vsnprintf which actually introduces this vulnerability via a format string. Format string vulnerabilities within variadic functions are caused when user-supplied input is passed as a format string without proper validation or sanitization, which can then lead to an adversary executing arbitrary code or leaking sensitive information.
Specifically, for the Zyxel vulnerability, an adversary provides a malicious command with an invalid IKE packet which ssh_vsnprintf will incorporate as part of a format string for the variadic function. Then the firmware makes a second call to ssh_vsnprintf to create a system command that will write the error message to a log file /tmp/sdwan_vpndebug.log. Following that, the firmware would use the system (root) to execute the malicious command. The patched firmware removes the call to the system in favor of writing directly to the log file with other functions.
To obtain remote code execution for the Proof-of-Concept exploit, Rapid7 worked to discover a way for a client (user/adversary) to provide input into the vulnerable function. Essentially, they needed a way to induce an error they could control that would be written to this log file. The answer to this question was IKE’s Notify payload. When the vulnerable Zyxel firmware decodes an IKE Notify packet when the message type is NO_PROPOSAL_CHOSEN. The data value for this packet is decoded by the firmware using DES-CBC, and then the decoded value is logged using the vulnerable function. However, and this is a big however, only the first 48 bytes of the data value were being decoded using DES-CBC, but the entirety of the data value was being copied over to the vulnerable function/log. This meant that Rapid7 could provide a valid 48-byte string and then concatenate their arbitrary command to the end to achieve remote code execution as the root user.
This Proof-of-Concept is documented and available to the public within Rapid7’s article as a Python3 script.
Assura’s Take
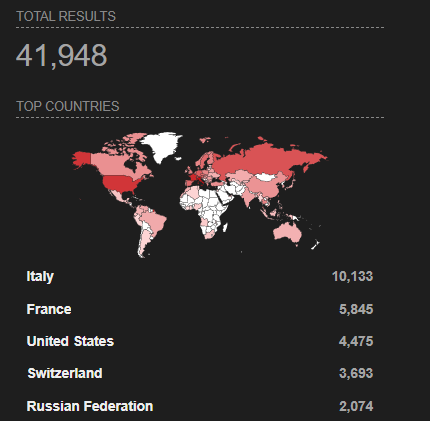
As with all pre-authentication remote code execution vulnerabilities, this has the potential to cause mayhem. It has yet to be seen how this access can be leveraged post-exploitation but root access to your edge security devices is never good. Based on a quick Shodan search, it appears that there are almost 42,000 Zyxel devices on the Internet, with 4,475 being in the U.S.
To limit the exploitation of this vulnerability in your organization, we recommend that you prioritize patching your Zyxel assets. Beyond patching, if you want to hunt for indicators of compromise in your Zyxel devices, you can search for the following entry in your /tmp/sdwan_vpndebug.log file: vpn_info: [cgnat] 4th cgnat convert wrong
Fixed versions of Zyxel’s firmware are as follows:
ATP – Firmware version 5.36
USG FLEX – Firmware version 5.36
VPN – Firmware version 5.36
ZyWALL/USG – Firmware version 4.73 Patch
References:
Rapid7 Analysis and POC – https://attackerkb.com/topics/N3i8dxpFKS/cve-2023-28771/rapid7-analysis
TRAPA Security – https://trapa.tw/
Zyxel Advisory – https://www.zyxel.com/global/en/support/security-advisories/zyxel-security-advisory-for-remote-command-injection-vulnerability-of-firewalls
